The national news cycle that followed the recent ransomware attack on Colonial Pipeline highlighted just how vulnerable corporations as well as key infrastructure systems are to this kind of crime. The U.S. Department of Justice says about $350 million in ransom money was paid to cybercriminals in 2020 – a jump of more than 300 percent from 2019 and they expect this trend to continue. But it’s not just the government and large organizations that need to protect data and keep networks cyber secure.
The government reports that 75 percent of all ransomware attacks are on small businesses. While fraudsters do target bigger companies looking for a big payoff, hackers frequently focus on small businesses which may have unprotected networks and a lack of IT professionals. This low-hanging fruit can be an easy, quick and financially-rewarding score.
Let’s learn what ransomware is, how it works and how a small business can prevent being exposed to this type of cyberattack.
What is ransomware?
Ransomware is a malware threat hackers use to infect computers and networks to encrypt files and block access by the victim. Once infected, ransom is demanded by the criminals for the victim to access the encrypted data. In some cases, even if a ransom has been paid to unlock the encrypted files, scammers will continue to target the victim by requiring additional payments, deleting a victim’s data, or declining to provide a working decryption key to restore access.

Paying ransom is not encouraged by the FBI and urges victims to report any ransomware incidents to the Internet Crime Complaint Center IC3 as soon as possible.
How does it work?
Computer files are encrypted when ransomware identifies the drives on an infected system and begins to encrypt the files within each drive. Generally, a unique extension is added to the encrypted files, such as .aaa, .micro, .encrypted, .ttt, .xyz, .zzz, .locky, to show the files have been encrypted.
Once file encryption has been completed, a separate file is created and displayed that contains instructions on how the victim can pay the ransom. If the payment is made, the fraudster may provide a cryptographic key to the victim so their files can be unlocked and accessed – but not always!
How does ransomware get on to computers?
Users can unknowingly download ransomware by opening an email attachment, clicking on a link or ad, or even accidentally visiting a website where malware is embedded. A very common way perpetrators send a ransomware attack is through phishing emails. These types of emails are disguised and will often appear as though they have been sent from a legitimate organization or someone the victim knows in order to entice the user to click on something in the email that’s actually malicious.
Another way malware is delivered to a computer is via “drive-by download” which is a program that is automatically downloaded from the internet without the user’s consent – and often without their knowledge. The malicious code may launch after download, even without user interaction and once the code has run, the computer becomes infected with ransomware.
How can a business protect data and networks?
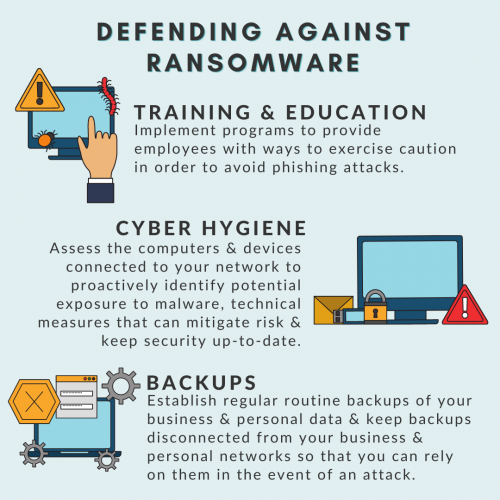
- Back up your computer regularly. Perform backups of your system and important files frequently, and verify the backups were completed. If your computer becomes infected, you may be able to restore your system to its previous state with your backups.
- Store your backups separately. It’s best practice to store your backups on a separate device such as an external hard drive that cannot be accessed from a network. Once the backup is completed, disconnect the separate device from the network or computer.
- Educate your organization. Provide regular cybersecurity awareness training to every member of the organization to ensure they are informed of current cybersecurity threats and the techniques used by perpetrators. To improve workforce awareness and be sure that training is being observed, organizations can test their associates with phishing assessments that simulate real-world scams.
For more tips, read Creating a Culture of Cybersecurity at Your Business.
What can be done to prevent ransomware infections?
- Practice caution when visiting websites. Be careful when clicking on links in emails, even if the sender appears to be someone you may know. Attempt to independently verify website addresses by either contacting your organization's helpdesk or performing a Google search of the organization who sent the email. Pay close attention to the links you click on, malicious website addresses often appear almost identical to legitimate sites. All the perpetrator does is add a slight variation in spelling or a different domain such as .net instead of .com at the end of the web address to try to trick you.
- Open email attachments cautiously. Be wary of opening attachments that are sent via email, particularly attachments that are compressed or ZIP files. Even if the sender is someone you think you know, it’s important to be cautious.
- Verify email senders. If you are unsure whether or not an email is legitimate, it’s best to verify the legitimacy by contacting the sender directly. If possible, refer to a previous email you received from the sender to ensure their contact information is authentic before reaching out to them.
- Stay informed. Remain informed about recent cybersecurity threats and stay up-to-date on ransomware techniques. The most recent information regarding known phishing attacks can be found through the Anti-Phishing Working Group. You can also sign up for CISA product notifications, which will email you when a new Alert, Analysis Report, Bulletin, Current Activity, or Tip has been published so you have the most timely information about security topics and threats.
- Use, maintain and update preventative software programs. Install antivirus software and firewalls to reduce malicious network traffic. Be sure they are up-to-date so they are working effectively.
How to respond to a ransomware infection
- Individual users: immediately contact your local FBI office for assistance.
- Organizations: immediately report ransomware incidents to your company helpdesk.
- Isolate the infected system. Be sure to remove the system that was attacked by ransomware from all networks including the computer’s Wi-Fi, Bluetooth, and any other networking capabilities. Also, ensure all shared files and drives are disconnected as well.
- Turn off all other computers and devices. Once removed from the network, power-off and separate the infected computer as well as any other computers or devices that share the same network – even if the other devices have not been encrypted. It’s possible that partially encrypted files can be recovered if turned off and separated from the infected computer. Secure all infected and potentially infected computers and devices in a central location and be sure to clearly label any that have been encrypted. The more cautious, the better!
- Keep backups secure. Ensure your backup data is offline and secure and scan your backup data with an antivirus program to check that it’s free of malware.
- All users: reset all system passwords once the ransomware has been removed. And report the incident to CISA for analysis.

StopRansomware.gov is the U.S. Government’s official website for resources to help tackle the ransomware challenge. And as a community bank, we also want to be a resource to help you protect your business from malicious attacks.
Visit the Lakeland Bank Identity Theft Center for additional tips and tricks to beat the scammers at their own game, read our blogs on the topic of Privacy & Cybersecurity or contact us at 866-224-1379.


